Page 21 - Layout 1
P. 21
ELECTRONIC
MEDICAL RECORDS
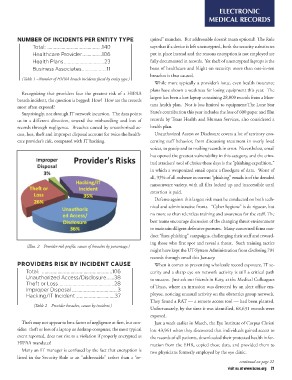
NUMBER OF INCIDENTS PER ENTITY TYPE quired” mandate. But addressable doesn’t mean optional! The Rule
Total: ..........................................140 says that if a device is left unencrypted, both the security substitutes
Healthcare Provider...............106 put in place instead and the reasons encryption is not employed are
Health Plans ...............................23 fully documented in records. Yet theft of unencrypted laptops is the
Business Associates...................11 bane of healthcare and blight on security: more than one-in-ten
breaches is thus caused.
(Table 1 –Number of HIPAA breach incidents faced by entity type.)
While more typically a provider’s issue, even health insurance
Recognizing that providers face the greatest risk of a HIPAA plans have shown a weakness for losing equipment this year. The
breach incident, the question is begged: How? How are the records largest has been a lost laptop containing 28,000 records from a Mon-
most often exposed? tana health plan. Nor is loss limited to equipment:The Lone Star
State’s contribution this year includes the loss of 600 paper and film
Surprisingly, not through IT network incursion. The data points records by Texas Health and Human Services, also considered a
us in a different direction, toward the mishandling and loss of health plan.
records through negligence. Breaches caused by unauthorized ac-
cess, loss, theft and improper disposal account for twice the health- Unauthorized Access or Disclosure covers a lot of territory con-
care provider’s risk, compared with IT hacking. cerning staff behavior, from discussing treatment in overly loud
voices, to gossip and to mailing records in error. Nevertheless, email
(Illus. 2 – Provider risk profile, causes of breaches by percentage.) has opened the greatest vulnerability in this category, and the crim-
inal attackers’ tool of choice these days is the “phishing expedition,”
PROVIDERS RISK BY INCIDENT CAUSE in which a weaponized email opens a floodgate of data. Worst of
Total: ......................................................106 all, 93% of all malware in current “phishing” emails is of the dreaded
Unauthorized Access/Disclosure......38 ransomware variety, with all files locked up and inaccessible until
Theft or Loss...........................................28 extortion is paid.
Improper Disposal ...................................3
Hacking/IT Incident ..............................37 Defense against this largest risk must be conducted on both tech-
nical and administrative fronts. “Cyber hygiene” is de rigueur, but
(Table 2 – Provider breaches, causes by incident.) no more so than relentless training and awareness for the staff. The
best teams encourage discussion of the changing threat environment
Theft may not appear to be a factor of negligence at first, but con- to maintain diligent defensive postures. Many concerned firms con-
sider: theft or loss of a laptop or desktop computer, the most typical duct “faux-phishing” campaigns, challenging their staff and reward-
event reported, does not rise to a violation if properly encrypted as ing those who first spot and reveal a threat. Such training tactics
HIPAA mandates! might have kept the UT-System Administration from disclosing 794
records through email this January.
Many an IT manager is confused by the fact that encryption is
listed in the Security Rule as an “addressable” rather than a “re- When it comes to preventing wholesale record exposure, IT se-
curity and a sharp eye on network activity is still a critical path
to success. Just ask our friends in Katy, at the Medical Colleagues
of Texas, where an intrusion was detected by an alert office em-
ployee, noticing unusual activity on the obstetrics group network.
They found a RAT — a remote access tool — had been planted.
Unfortunately, by the time it was identified, 68,631 records were
exposed.
Just a week earlier in March, the Eye Institute of Corpus Christi
lost 43,961 when they discovered that individuals gained access to
the records of all patients, downloaded their protected health infor-
mation from the EHR, copied those data, and provided them to
two physicians formerly employed by the eye clinic.
continued on page 22
visit us at www.bcms.org 21